We have created a comprehensive Security Operations Center (SOC) framework to help you keep your SOC up with the time

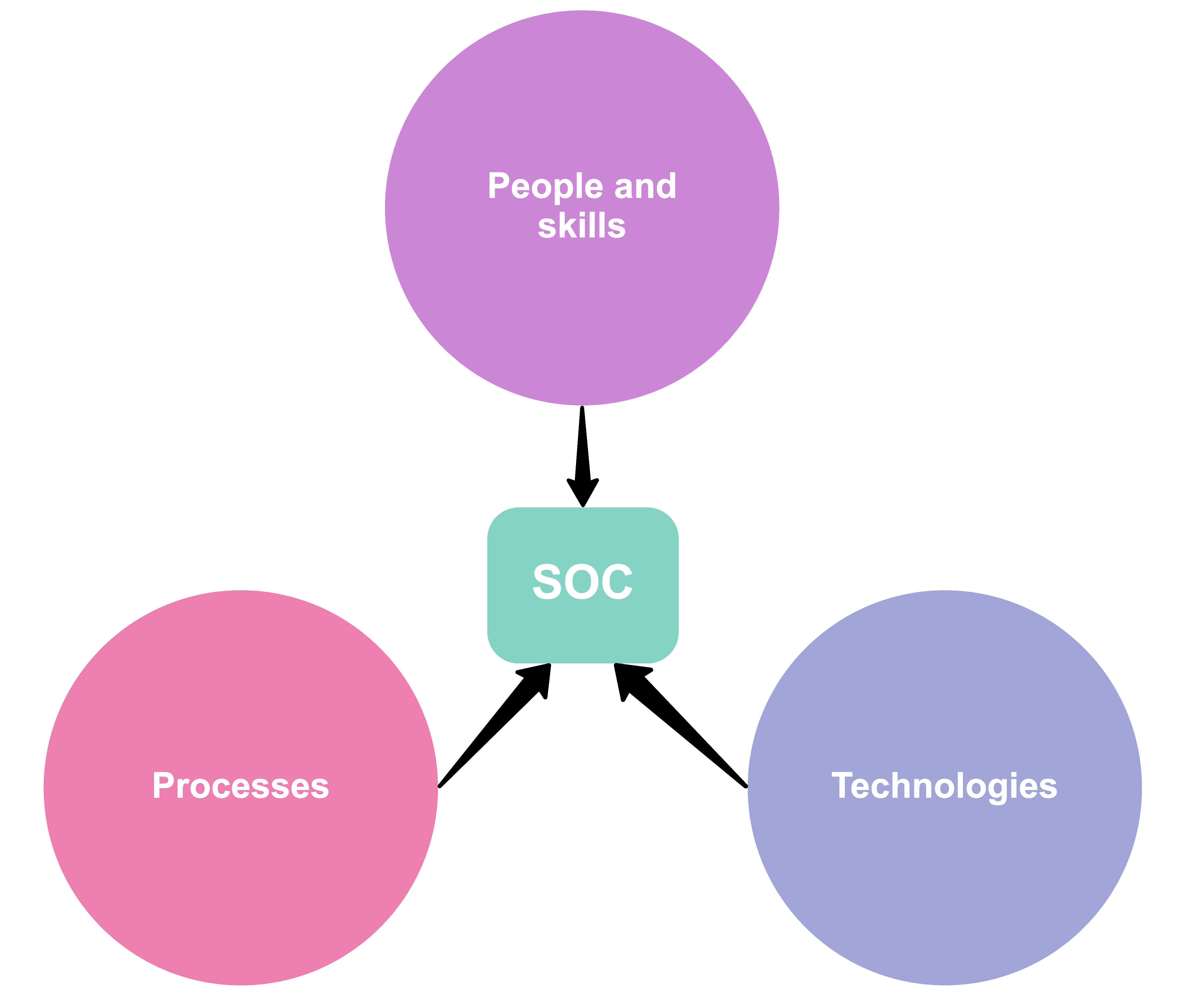
Let us transform your SOC by:
Implementing the necessary SOC Tools and Technologies
Defining clear processes and standards
Filling the roles with skilled employees and ensure continuous training
Technologies
SOC’s success depends on collection of the right data, correlation, detection, analysis and management technologies:
- Security Information Event Management (SIEM)
- Vulnerability scanner
- Network Intrusion Detection and Prevention
- Threat Hunting
- Threat intelligence
- Security Orchestration, Automation and Response (SOAR)
- KPI Analysis and Reporting
Processes
To ensure continuous quality alerting, key processes should be defined a SOC analyst follows (eg. in form of checklists or playbooks) to ensure no important tasks fall through the cracks.
- Event classification & Triage
- Prioritisation, Analysis & Escalation
- Remediation & Recovery
- Assessment & Review
- Reporting & Documentation
- Build Knowledge base and ensuring knowledge transfer
People and skills
The best tools, technologies and processes will not be effective without skilled staff. Continuous formal, vendor-specific and internal trainings are key!
Roles and responsibilities:
- Tier 1: Alert Analyst
- Tier 2: Incident Responder
- Tier 3: Subject Matter Experts (SME)
- Tier 4: SOC Manager
- SOC Head
